MrPentester helped us when our website was under continuos attack and we were demanded ransom as payment, but MrPentester team took the challenge and restored our services within 3 hours and eliminated all loopholes within a day. Highly recommended.
Secure Source Code review
You don't know which vulnerabilities are going to production in your code! Well, Now you can!
Source code review plays a key role as we analyse your code to full extent and check for any kind of vulnerabilities the script has been exposed to. There can be bugs anywhere in your script and can be fixed manually and/or with the help of automated systems, as per the requirement. You have no idea what could go in production with your source code, if any missed validation could lead to an attack! Better to fix now, than to regret later.! Reach out to us!
Talk To a Security Expert
We Will Help You To Choose The Best Plan!
Secure Source Code review

Secure source code review with Critical & efficient approach to meet your organizational security needs & production safety.
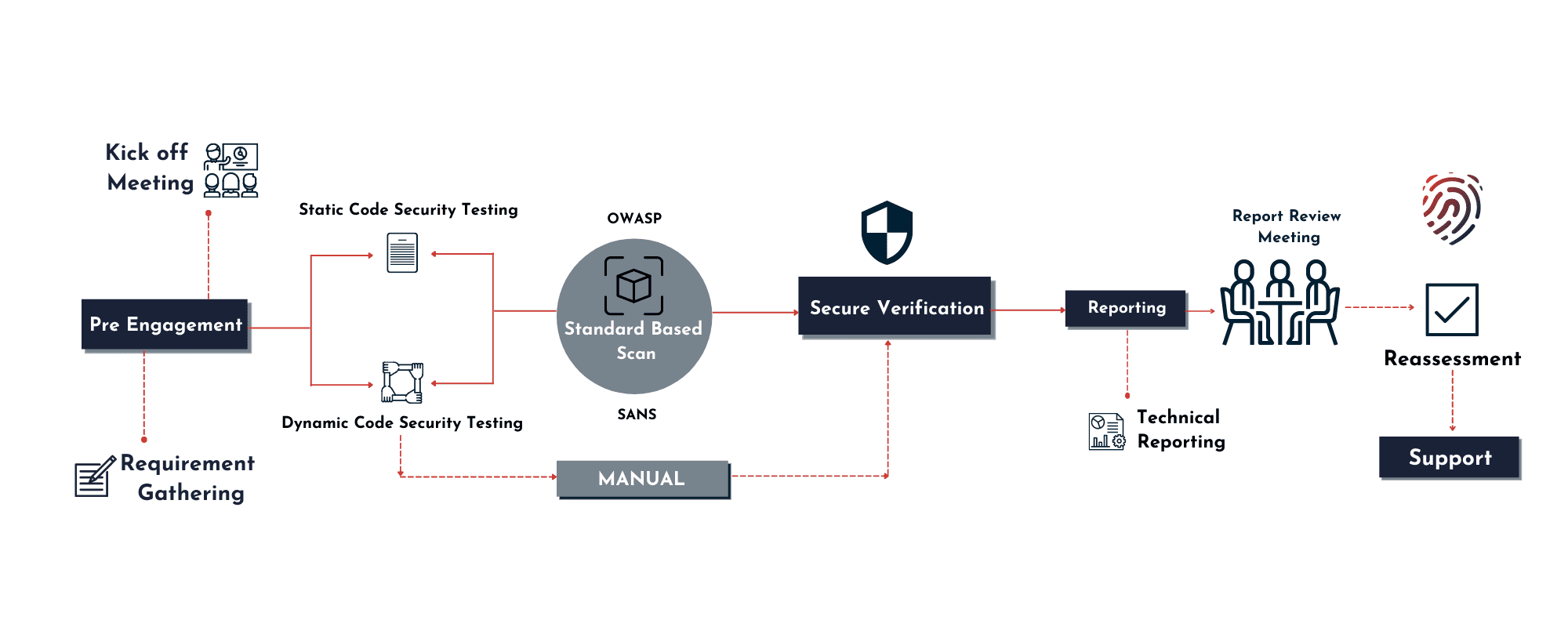
Approach for Secure Source Code review
Core Expertise
Our pentesting team stays up-to-date by keeping themselves on track as they work over bug fixes and remediation. They are not just experts at what they do, they also follow smart prioritization to keep you on top. We follow the approach to, Gather enough information about the vulnerability the client has been exposed to and find suitable solutions to fix the issue as quickly as possible. There could be instances when the code taken from open source could contain known CVEs, our expertise helps in preventing any such damages!
Right Approach
Our team brainstorms for solutions and uses the best possible methodologies for tracking down vulnerabilities and later assisting in mitigating them. Thorough check up is done in order to integrate into the organization’s secure software development cycle.
Modern Outlook
Manual testing is in alignment with Powerful Open Web Application Security Project (OWASP) standards & other accredited standards. Any flaws in the feature and design are also looked upon for better and efficient functioning. SAST tools are used in order to ensure a secure way of resolving issues.
Partners forever
We believe in creating everlasting relationships of unbreakable security bond, our AI based systems instantly alert for any critical findings in order to take quick actions!
- Core Expertise
Core Expertise
Our pentesting team stays up-to-date by keeping themselves on track as they work over bug fixes and remediation. They are not just experts at what they do, they also follow smart prioritization to keep you on top. We follow the approach to, Gather enough information about the vulnerability the client has been exposed to and find suitable solutions to fix the issue as quickly as possible. There could be instances when the code taken from open source could contain known CVEs, our expertise helps in preventing any such damages! - Right Approach
Right Approach
Our team brainstorms for solutions and uses the best possible methodologies for tracking down vulnerabilities and later assisting in mitigating them. Thorough check up is done in order to integrate into the organization’s secure software development cycle. - Modern Outlook
Modern Outlook
Manual testing is in alignment with Powerful Open Web Application Security Project (OWASP) standards & other accredited standards. Any flaws in the feature and design are also looked upon for better and efficient functioning. SAST tools are used in order to ensure a secure way of resolving issues. - Partners forever
Partners forever
We believe in creating everlasting relationships of unbreakable security bond, our AI based systems instantly alert for any critical findings in order to take quick actions!
How we differ
MrPentester's Source code security review is not just a set of checklist to run through or a mere scan, but an exclusive experience to safeguard your business reputation & applications / products!
- Grouping each vulnerability into development issues and business logic issues.
- Efficient approach & advanced methodologies to protect your Infrastructure
- Transparent visibility on the project status & updates.
- High quality, fully segregated and top standard report quality to present to the CXO.
- Integrated secure coding campaign for developers.
- Detailed & simplified reports for all the re-assessments with Track.
- Detailed issue track sheets with smart compliance mapping