MrPentester helped us when our website was under continuos attack and we were demanded ransom as payment, but MrPentester team took the challenge and restored our services within 3 hours and eliminated all loopholes within a day. Highly recommended.
Cloud security assessment
Don't Just Deploy, Protect your cloud Infrastructure...
Cloud computing has been at all time high, with nearly every organizations now using it, there could be diverse set of risks and vulnerabilities coming from impementation faults, misconfigurations and more. You need to protect your cloud infra against theft, leakage & deletion.
Talk To a Security Expert
We Will Help You To Choose The Best Plan!
Cloud security assessment

Cloud security with 360 degree approach to protect, secure & empower your cloud computing practices.
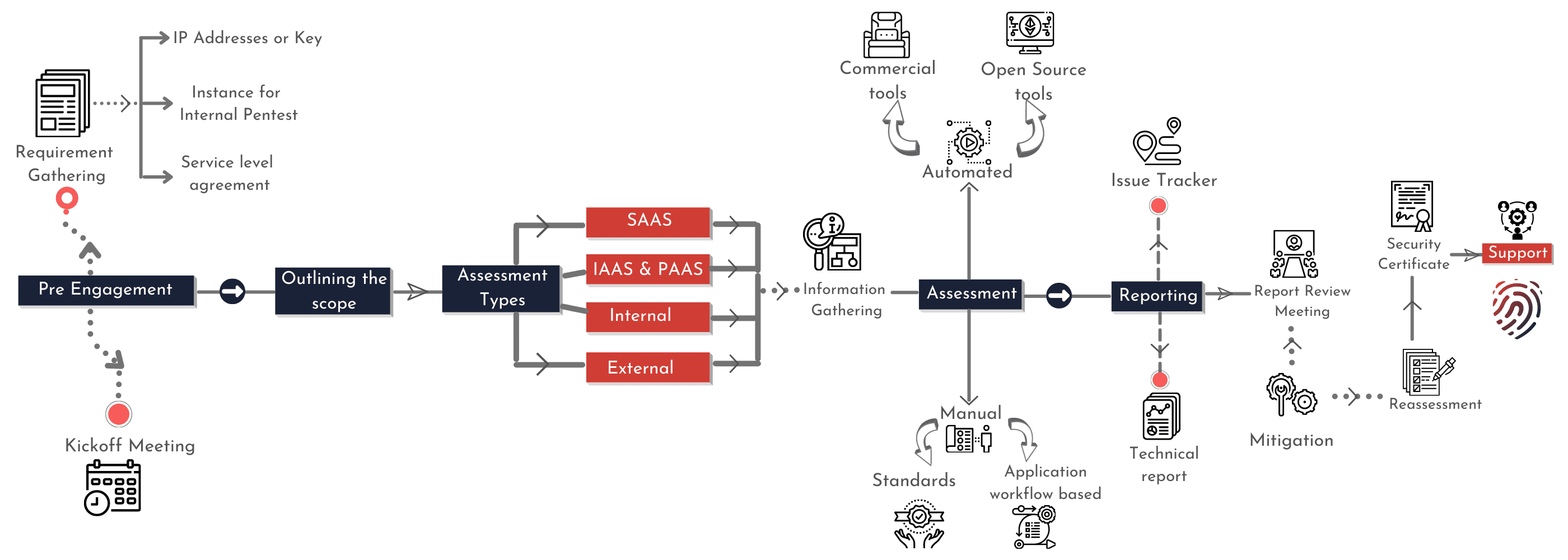
Approach for Cloud security assessment
Core Expertise
Our pentesting team stays up-to-date by keeping themselves on track as they work over bug fixes and remediation. They are not just experts at what they do, they also follow smart prioritization to keep you on top.
Right Approach
Our team brainstorms for solutions and uses the best possible methodologies for tracking down vulnerabilities and later assisting in mitigating them.
Discover & Fix
Discover the most vulnerable route through which the applications hosted on cloud can be compromised. Identify any loopholes that could lead to the theft of sensitive data from cloud applications. Work on instant fixes for above and educating team on preventing the same.
Modern Approach
We follow SAST and DAST methods in order to fix the security related to the cloud. We also use proper SCA tools in order to carry out precise pentesting and fix the problem. In-depth and thorough analysis of the cloud systems.We also provide security guidance to our clients.
Partners forever
We believe in creating everlasting relationships of unbreakable security bond, our AI based systems instantly alert for any critical findings in order to take quick actions!
- Core Expertise
Core Expertise
Our pentesting team stays up-to-date by keeping themselves on track as they work over bug fixes and remediation. They are not just experts at what they do, they also follow smart prioritization to keep you on top. - Right Approach
Right Approach
Our team brainstorms for solutions and uses the best possible methodologies for tracking down vulnerabilities and later assisting in mitigating them. - Discover & Fix
Discover & Fix
Discover the most vulnerable route through which the applications hosted on cloud can be compromised. Identify any loopholes that could lead to the theft of sensitive data from cloud applications. Work on instant fixes for above and educating team on preventing the same. - Modern Approach
Modern Approach
We follow SAST and DAST methods in order to fix the security related to the cloud. We also use proper SCA tools in order to carry out precise pentesting and fix the problem. In-depth and thorough analysis of the cloud systems.We also provide security guidance to our clients. - Partners forever
Partners forever
We believe in creating everlasting relationships of unbreakable security bond, our AI based systems instantly alert for any critical findings in order to take quick actions!
How we differ
MrPentester's Cloud security assessment is not just a set of checklist to run through, but an exclusive experience to safeguard your business reputation & Cloud Infrastructure!
- Identifying detailed security issues with intelligent recommendations on realtime basis.
- Efficient approach & advanced methodologies to protect your Infrastructure
- Transparent visibility on the project status & updates.
- High quality, fully segregated and top standard report quality to present to the CXO.
- Integrated secure coding campaign for developers.
- Detailed & simplified reports for all the re-assessments with Track.
- Detailed issue track sheets with smart compliance mapping